VisitorZz
Facebook Fanpage
Showing posts with label pc tips and tricks. Show all posts
| How to stop aplications getting started during phone Boot? In c:/system/ there is a folder named "recogs", this folder contains.mdl files will act as a shortcut to the actual application. During system startup all these mdl files will be read and started up. If you edit this file to point to nonexisting file then the application wont startup again. Don't delete the files as they will be recreated next time you open the application manually. |
| 10 reasons why PCs crash U must Know Fatal error: the system has become unstable or is busy," it says. "Enter to return to Windows or press Control-Alt-Delete to restart your computer. If you do this you will lose any unsaved information in all open applications." You have just been struck by the Blue Screen of Death. Anyone who uses Mcft Windows will be familiar with this. What can you do? More importantly, how can you prevent it happening? 1 Hardware conflict The number one reason why Windows crashes is hardware conflict. Each hardware device communicates to other devices through an interrupt request channel (IRQ). These are supposed to be unique for each device. For example, a printer usually connects internally on IRQ 7. The keyboard usually uses IRQ 1 and the floppy disk drive IRQ 6. Each device will try to hog a single IRQ for itself. If there are a lot of devices, or if they are not installed properly, two of them may end up sharing the same IRQ number. When the user tries to use both devices at the same time, a crash can happen. The way to check if your computer has a hardware conflict is through the following route: * Start-Settings-Control Panel-System-Device Manager. Often if a device has a problem a yellow '!' appears next to its description in the Device Manager. Highlight Computer (in the Device Manager) and press Properties to see the IRQ numbers used by your computer. If the IRQ number appears twice, two devices may be using it. Sometimes a device might share an IRQ with something described as 'IRQ holder for PCI steering'. This can be ignored. The best way to fix this problem is to remove the problem device and reinstall it. Sometimes you may have to find more recent drivers on the internet to make the device function properly. A good resource is www.driverguide.com. If the device is a soundcard, or a modem, it can often be fixed by moving it to a different slot on the motherboard (be careful about opening your computer, as you may void the warranty). When working inside a computer you should switch it off, unplug the mains lead and touch an unpainted metal surface to discharge any static electricity. To be fair to Mcft, the problem with IRQ numbers is not of its making. It is a legacy problem going back to the first PC designs using the IBM 8086 chip. Initially there were only eight IRQs. Today there are 16 IRQs in a PC. It is easy to run out of them. There are plans to increase the number of IRQs in future designs. 2 Bad Ram Ram (random-access memory) problems might bring on the blue screen of death with a message saying Fatal Exception Error. A fatal error indicates a serious hardware problem. Sometimes it may mean a part is damaged and will need replacing. But a fatal error caused by Ram might be caused by a mismatch of chips. For example, mixing 70-nanosecond (70ns) Ram with 60ns Ram will usually force the computer to run all the Ram at the slower speed. This will often crash the machine if the Ram is overworked. One way around this problem is to enter the BIOS settings and increase the wait state of the Ram. This can make it more stable. Another way to troubleshoot a suspected Ram problem is to rearrange the Ram chips on the motherboard, or take some of them out. Then try to repeat the circumstances that caused the crash. When handling Ram try not to touch the gold connections, as they can be easily damaged. Parity error messages also refer to Ram. Modern Ram chips are either parity (ECC) or non parity (non-ECC). It is best not to mix the two types, as this can be a cause of trouble. EMM386 error messages refer to memory problems but may not be connected to bad Ram. This may be due to free memory problems often linked to old Dos-based programmes. |
Another useful way to resolve video problems is to go to * Start-Settings-Control Panel-System-Performance-Graphics Here you should move the Hardware Acceleration slider to the left. As ever, the most common cause of problems relating to graphics cards is old or faulty drivers (a driver is a small piece of software used by a computer to communicate with a device). Look up your video card's manufacturer on the internet and search for the most recent drivers for it. 6 Viruses Often the first sign of a virus infection is instability. Some viruses erase the boot sector of a hard drive, making it impossible to start. This is why it is a good idea to create a Windows start-up disk. Go to * Start-Settings-Control Panel-Add/Remove Programs Here, look for the Start Up Disk tab. Virus protection requires constant vigilance. A virus scanner requires a list of virus signatures in order to be able to identify viruses. These signatures are stored in a DAT file. DAT files should be updated weekly from the website of your antivirus software manufacturer. An excellent antivirus programme is McAfee VirusScan by Network Associates ( www.nai.com). Another is Norton AntiVirus 2000, made by Symantec ( www.symantec.com). 7 Printers The action of sending a document to print creates a bigger file, often called a postscript file. Printers have only a small amount of memory, called a buffer. This can be easily overloaded. Printing a document also uses a considerable amount of CPU power. This will also slow down the computer's performance. If the printer is trying to print unusual characters, these might not be recognised, and can crash the computer. Sometimes printers will not recover from a crash because of confusion in the buffer. A good way to clear the buffer is to unplug the printer for ten seconds. Booting up from a powerless state, also called a cold boot, will restore the printer's default settings and you may be able to carry on.
|
| Anyone who says the Consumer Electronics Show is waning hasn't been packed like a sardine waiting for the Central Hall doors to open at LasVegas Convention Center on the first day of CES.Despite the absence of electronics market leaders like Apple, and the imminent exit of PC heavy hitter Microsoft, CES is still going incredibly strong with more than 2,700 exhibitors in over 1.8 million square feet of space. From giant multi-level booths with built-in coffee bars in the LVCC to stand-alone tables in hotel suites up the strip, there are a lot of products on display here at CES. More than we care to count, and many of which we'll have trouble remembering in June. What really matters are the ones we know will help set the tone for the industry in the coming 12 months. If you want to read all that we've written aboutthe show this week, check out our CES page , or allow us to cut through all the noise and break it down for you right here with the best products we've seen at CES. BEST TABLET Winner: Asus Eee Pad Transformer Prime TF700  The best tablet at CES is one I've never actually touched. But Asus's Eee Pad Transformer Prime is currently the best Android tablet available, with its quad-core processor, laptop attachment, and now Android 4.0. Plenty of other Android 4.0 tablets are cropping up here at CES, but so far none of them are quite as elegant and well-built as the Transformer Prime. So the new Transformer Prime just announced—which is essentially the existing model, but with a stunningly high-res 1080p screen—is going to remain the benchmark by which other Android tablets are measured. –Sascha Segan Runner Up: Ainovo Novo 7 Basic
|
| How To Repair Detectable But Corrupt USB Drive- Have you suddenly encountered with the problem that when youplug in your USB drive,the Removable media shows up but when you try to open it, it returns with the message"Please insert a disk in to drive H:" By applying this simple method you’ll have 80% chance to get back your USB drive hardware. This works only in the above error condition. If the windows doesn’t detect your USB drive, then there is probably flaw in the USB media. Please keep in mind that, you’ll have to lose your data when following this tutorial. Plug in your USB drive. Go to Start>My Computer, right click on My Computer icon and click on Manage menu Computer Management window will pop up. Click on Disk management under Storage tree menu. Now at the right side of the window right click on your removable media. (unlike the image below, it will show unknown information), right click on your removable media and choose Change Drive Letter and Paths. Now in new window choose any drive later that is not taken by any media (M:, N: , :K: etc). Click on ok button and close the management window. Try opening your pendirve. There may be the chance to have your pendrive recovered if this method worked. If the problem still prevails then follow the above tutorial but instead of choosing Changedrive letter and paths, choose Fomrat and give a quick format to it. Thats it.. Please comment here Is That Useful Tread??? |
| 1.rapid shut down window while shutting down window. open task manager(ctr+alt+del), select shut down tab. and press ‘ ctrl ‘ key while select turn off from dis tab. u r window will rapidly shut down. speed up ur shut down !! start regedit. navigate to hkey_local_ machine/system/ currentcontrolset/control. click on the “control” folder. select “ waittokillservicetimeout” right click on it and select modify. set it a value lower than 2000 (mine is set to 200). and ! like previous versions of windows, it takes long time to restart or shutdown windows xp when the “exit windows” sound is enabled. to solve this problem you must disable this useless sound. click start button then go to settings - control panel - sound,speech and audio devices - sounds and audio devices - sounds, then under program events and windows menu click on “exit windows” sub-menu and highlight it.now from sounds you can select,choose “none” and then click apply and ok. now you can see some improvements when shutting down. *sharing m0de* |
In facebook in any comment box (not status) write
@[515:]
@[515:]
Copy the Code
... (You can change the digits like 123, 345 etc.) and submit to see what happens....| Today i got a trick to bypass adf.ly links on our mobile. I have tested it for several times and get success. Go to this site, enter your links has to be bypass and you are redirected to your desired link directly. Enjoy. . . http://adfly.simplaza.net/ |
| first go to multime.org and register there second upload your jar application by using my midlet tab third create your project fourth after creating your project click on your project add your jar application by using add midlet tab fifth build your project last download your project.......  |
| If you want to download videos from youtube to your pc or mobile, then there is a very simple and easy method.Just follow these simple steps: Go to youtube video page, the video you want to download. Just remove 'www.' from the video url(in address bar) and add 'ss' and press enter. A new page will open. Choose the format like flv 240p,360p,mp4 720p,etc. Your download will started. In case you want to download video from your mobile phone replace'm.' with 'ss' and choose the video format. For example in pc video url- http://www.youtube.com/watch?v=b ... 2bf17a2YMAAAAAAADAA Replace 'www.' with 'ss' http://ssyoutube.com/watch?v=b3H ... 2bf17a2YMAAAAAAADAA In case of mobile video url- http://m.youtube.com/watch?v=0LrT8N02vys Remove m. & Add ss http://ssyoutube.com/watch?v=0LrT8N02vys ANOTHER WAY The method can be applied if you have already streamed a video fully. actually the streamed video gets stored on your system you just have to access it by a software called Unlocker. In the below methods installation of java is required. Download Java from www.sun.com Insert Into URL : For this kind of sites you have to add some codes before the youtube.com portion of the video you want to download. Before The rest of the files are quite the same.Here are some: 1 - SaveYouTube : Formerly known as (Kissyoutube) , supports HD Download. 2 – Det URL : (pwnyoutube.com…), redirects you to a site with much download options to download and convert using other services. Has a nice Bookmarklet tool. 3 - WantYouTube : (wantyoutube.com…..) Requires Java , supports All Downloads including MP3 4 – Keep-Tube : ( keep-youtube.com….) requires java. supports HD and .MP3 . Got addon and bookmarklet. Online Direct Download Services: These sites can help you get the download task done for you. 1 – TubeKeeper : Java Based.Supports HD Downloads. 2 - SaveTube : Java Based.Supports download as HD or mp3. 3 – SaveFrom : Supports HD , quick download links for 40+ web pages , Extension and bookmarklet for quick download. 4 – KeepVid : HD Support. Requires java for mp3 download. 5 – SaveVid : Requires Java, supports HD Download. Works best on chrome. 6 – YouConvertIt: Requires java. Might not work for some videos especially HD. 7 – SaveVideoDownload : Requires Java. Supports download as .FLV , .MP4 , .webm. 8 – DownloadYouTubeVideo : Java Based. Only FLV Supported. |
In this era of social networking it is very hard to remain away
from Facebook for a single day .There are many users who add
thousand of friends in begning,but after some time they want
to get rid of there account amd create a new account.They fail
to find the option to delete there account. Simple steps are given
below by which you can delete your Facebook account .
Instructions
1. Login to your Facebook account.
2. Click on the link given below
facebook.com/help/contact.php?show_form=delete_account
3. Now click on submit button.
4. After this don't login to your account for 90 days.
5. Than after 90 days,your Facebook account will be deleted completely.
from Facebook for a single day .There are many users who add
thousand of friends in begning,but after some time they want
to get rid of there account amd create a new account.They fail
to find the option to delete there account. Simple steps are given
below by which you can delete your Facebook account .
Instructions
1. Login to your Facebook account.
2. Click on the link given below
facebook.com/help/contact.php?show_form=delete_account
3. Now click on submit button.
4. After this don't login to your account for 90 days.
5. Than after 90 days,your Facebook account will be deleted completely.
| In this tutorial I am going to teach you howto reset your memory card password in easy step. Before we start you need to have X-plore (application used to explore your system files and folder even the hidden folders in your device) Step1 : Install X-Plore in your mobile. If you want to download X-Plore search around internet you can download free trail. Step2 : Open your X-plore apps and Press 0(Zero) and check which you have marked the "show the system files" Step3 : Once you done that now go to the following path C:/Sys/Data/Mmcstore Step4 : Once you reached there you need to press "3" under option to set it in the Hex-viewer Step5 : See the third column you will able to see a line of code ! TMSD02G (c??"?x???6?2?6?2?6). Just check the character between the "?" it is your password ie: 62626 Note: If you have not set the password, then you will not able to gain access to C:/Sys/Data Enjoy... |
| for this.. follow the steps step 1)First Login into your Facebook Account( click here facebook.com ). step 2)Next, Click here( facebook.com/about/messages <add http>) to Send a request. In the next window, click on “Request anInvitation” button. Thats it...It will take some time to get your account activated. You’ll get a message alert once it is accepted.once it is approved you can use that mail id(yourname@facebook.com) You can then select your Username for your facebook email which will be “Username@facebook.com” you can share your Facebook email ID with your friends.it will directly land in messages section of your Facebok account. |
| Edited by Dr1358 at 21-1-2012 01:25 www.joinme.com Hi to all.im here for tell you the best site LogMeIn, Inc. ("LogMeIn"), respects your privacy and is committed to protect the personal information that you share with us. Generally, you can browse through our website without giving us any information about yourself. This policy describes how we collect and use your personal information when we need your personal information to provide services that you request or when you choose to provide us with your personal information through our LogMeIn.comwebsite.Information CollectionPersonal information means any information that may be used to identify an individual, including, but not limited to, a first and last name, company name, email address, telephone number, postal or other physical address, birth date, gender, occupation, a credit card number (including expiration date) to process payment for products and/or services and such other information when needed to provide a service that you requested. Certain of our product and services also store connection or session information such as time/dateand length of collection, IP address, chat logs and technician information. As you navigate through this site, certain anonymous information can be passively collected (that is, gathered without your actively providing the information) using various technologies, such as cookies, Internet tags or web beacons, and navigational data collection (log files, server logs, clickstream). Your internet browser automatically transmits to this site some of this anonymous information, such as the URL of the web site you just came from and the Internet Protocol (IP) address and the browser version your computer is currently using; the date and time youaccess the site and the pages that you access while at the site. This information is used for internal/external marketing purposes, to analyze trends and to improve the site. This site may also collect anonymous information from your computer through cookies and internet tags or web beacons. You mayset your browser to notify you when a cookie is sent or to refuse cookies altogether, but certain features of this site might not work without cookies. LogMeIn collects personal informationwhen you elect to use our software ona free trial basis or purchase a license or an upgrade. LogMeIn only uses suchinformation if it has been collected in accordance with acceptable privacy practices consistent with this Policy and applicable laws.Choice/Opt-OutYou may elect to "opt out" of receivingdirect marketing or market research information. This means we assume you have given us your consent to collect and use your information in accordance with this Policy unless youtake affirmative action to opt out at the point of collection. Opt-out is the means by which you give us, or decline to give us, your consent to use your personal information for the purposes covered by the opt-out choice. You may opt out at the point ofcollection when personal information is collected, or you may do so at any time by sending an email request to support@LogMeIn.com(please indicate "Opt Out" in the subject line) or by sending a written request to the address provided below. In some cases, we will provide you with the opportunity to "opt in". This means we will require your affirmative actionto indicate your consent before we use your information for purposes other than the purpose for which it was submitted. |
| Cookies and Tracking TechnologyA cookie is a small data file that certain Web sites write to your hard drive when you visit them. Cookies cannot be used to run programs or deliver viruses to your computer. A cookie file can contain information such as a user ID that the site uses to track the pages you've visited, but the only personal information a cookie can contain is information you supply yourself. A cookie can't read data off your hard disk or read cookie files created by other sites. Cookies save you time, for example, if you personalize a web page, or navigate within a Site, a cookie recalls your specific information on subsequent visits. LogMeIn's website also uses cookies to track user traffic patterns. We do this in order to determine the usefulness of our website informationto our users and to see how effective our navigational structure is in helping users reach that information. You may accept or decline cookies. Most web browsers automatically accept cookies, however you can modify your browser setting to decline cookies. In addition to cookies, our site uses a variety of technical methods for tracking purposes, including web beacons. Web beacons are small pieces of data that are embedded in images on the pages of web sites. LogMeIn's also uses these technical methods to analyze the traffic patterns on our web site, such as the frequency with which our users visit various parts of our web site.How We Use Information CollectedLogMeIn uses personally identifiable information for several general purposes: to fulfill your requests for certain products and services, to keep you up to date on the latest product announcements, software updates, special offers or other information we think you'd like to hear about either from us or from our business partners,and to better understand your needs and provide you with better services. We may also use your information to send you promotional materials aboutgoods and services (including special offers and promotions) either offered by LogMeIn or offered by third parties.You may opt out of receiving these communications.Information Sharing and DisclosureOur web site provides you the opportunity to opt-in to receive communications from us when you elect to use our software on a free-trial basis, or purchase a new license or an upgrade. Further, when you receive the requested communication, you are given the opportunity to unsubscribe from receiving any future communication or to change your information. Unless you opt-in, LogMeIn will not transfer your personal information to third parties, except we may transfer your personal information without your consent to the extent required to do so by law or in the good faith belief that such action is necessary to: a. conform to the edicts of law or comply with legal process served on LogMeIn or the site; b. protect or defend the rights or property of LogMeIn, c. act in urgent circumstances to protect the personal safety, property, or privacy of LogMeIn's employees, users of LogMeIn's products or service, or members of the public, or d. effect a transaction, restructuring or proceeding that transfers to a third party the assets or line of business to which the information pertains |
| Edited by dky at 21-1-2012 20:22 Scientists at IBM have apparently discovered the absolute minimum amount of data required to store a bit of data: a dozen atoms. They stored code for the word "think" using under 100 iron atoms, using a scanning tunneling microscope to engineer antiferromagnetically coupled atoms that store data for hours at low temperatures. Researchers at IBM's (NYSE: IBM) Almaden Labs have created a 12-atom magnetic memory bit, in a continuation of work on atomic-level memory storage first posited in 1959 by American physicist Richard Feynman . This image shows a magnetic byte imaged five times in different magnetic states to store the ASCII code for each letter of the word"THINK," a corporate mantra used byIBM since 1914. The team achieved this using 96 iron atoms -- one bit was stored by 12 atoms and there are eight bits in each byte. Disk drives currently use about 1 million atoms to store a single bit of information, according to IBM. The scientists used antiferromagnetism to achieve their result. They stored the ASCII code for the word "Think" on 96 iron atoms using this approach. "This atomic storage is not something you'll see coming to a Best Buy (NYSE: BBY) near you, but it's an indication of the way the IT industry continues to find innovativeways around the limitations of storage technology," Charles King, principal analyst at Pund-IT , told TechNewsWorld. "What's interesting about this is, people have wondered where the brick wall is -- the maximum amount of data that can be stored magnetically," Jim Handy, an analyst at Objective Analysis , told TechNewsWorld. "The researchers worked this backwards, to find out what's the minimum amount of storage we'll need." IBM did not respond to requests to comment for this story. How IBM's Process Works The IBM scientists used a scanning tunneling microscope (STM) to engineer 12 antiferromagnetically coupled atoms that stored a bit of data for hours at low temperatures. In the simplest terms, the spin of electrons in atoms of antiferromagnetic materials aligns in a regular pattern with those of their neighbors pointing in opposite directions. Visualize a flat surface with arrows in a 4 by 4 pattern -- four rows and four columns. The arrows in each row and column alternately point upor down, so an arrow pointing up will have its neighbors to the sides and immediately above and below pointing down, for example. Antiferromagnetic order exists at low temperatures, and vanishes at and above the Neel temperature . This temperature depends on the material used. In order to store the ASCII code for the word "Think," the researchers had to image a magnetic byte (one byte = 8 bits = 96 atoms at 12 atomsper bit) five times in different magnetic states. The Long, Hard Road to Market Given that the process of writing data onto a magnetic byte is tortuous, and can only be carried outat low temperatures, it's not likely that IBM will be able to commercialize its atomic storage technology any time soon. "With an announcement like this, you'd expect a five- to 15-year horizon with risk at the back end," Rob Enderle, principal analyst at the Enderle Group , told TechNewsWorld."Manufacturing to scale is often a very difficult problem to solve with atechnology like this, which is why the very wide range." Come Play With My STM A scanning tunneling microscope is an instrument used to image surfaces at the atomic level. IBM Zurich researchers Gerd Binnig and Heinrich Rohrer developed the device in 1981 and won the Nobel Prize in Physics in 1986 for it. The STM is based on the concept of quantum tunneling. The atomic storage developed by IBM researchers follows on from previous experiments using the STM.
|
Battery life has always been a problem when it comes to smartphones, we have been talking about solar powered smartphones from quite some time now, but have never come up with a good solution, but a research team has come up with a new concept of OLED displays which have solar cells embedded in them, and this really looks like the perfect solution, at least for now.
It is sure not many of us spend most of our time outside in the sun, but we do go out for lunch and travel to work everyday, this new display developed by these researchers charges the phone by itself when exposed to sunlight. The lead researcher of thistproject Arman Ahnood also mentions that these cells also consume the light emitted by the display to charge itself, which indirectly means that more you keep the screen on or use your device the phone will charge itself, this concept sounds really greatand exciting as a perfect cure for low battery life in smartphones today.
Though the efficiency of the cells capturing light emitted by the display is around 11-18% which results to around 5 milliwatts of extra power on a 3.7″ display, you will be getting around 15- 20 minutes of extended battery life, and if you are using it with a bigger display like the Galaxy Note or the Galaxy Nexus then you might get better battery life, you can also think of taking breaks outside the office in sunlight which will help you charge your phone.
It is sure not many of us spend most of our time outside in the sun, but we do go out for lunch and travel to work everyday, this new display developed by these researchers charges the phone by itself when exposed to sunlight. The lead researcher of thistproject Arman Ahnood also mentions that these cells also consume the light emitted by the display to charge itself, which indirectly means that more you keep the screen on or use your device the phone will charge itself, this concept sounds really greatand exciting as a perfect cure for low battery life in smartphones today.
Though the efficiency of the cells capturing light emitted by the display is around 11-18% which results to around 5 milliwatts of extra power on a 3.7″ display, you will be getting around 15- 20 minutes of extended battery life, and if you are using it with a bigger display like the Galaxy Note or the Galaxy Nexus then you might get better battery life, you can also think of taking breaks outside the office in sunlight which will help you charge your phone.
if you have sensitive or important data stored on a particular disk drive that you don’t want anyone to see, a great way to hide it is to remove the drive letter assigned to a particular mounted volume. With Windows XP, you can achieve this easily using nothing more than the Command Prompt. Here’s how:
Click Start -> Run (This brings up the Run dialog box)
Type cmd and press Enter (This brings up the Windows Command Prompt
Type diskpart in the command prompt and press Enter (This launches the Diskpart utility within the Command Prompt window)
Now type list volume (This displays a list of all mounted volumes on your computer and their associated drive letters)
Type select volume 1 (or select any other volume as where the drive is present)
Now type remove letter R (Note: This sometime requires a reboot)
Diskpart will now remove the drive letter.
The drive will no longer be available via Windows Explorer or My Computer.
Unhide
Now, should you want to unhide the drive and make it accessible again, just repeat the above process. But instead of typing remove letter R, type assign letter R
Click Start -> Run (This brings up the Run dialog box)
Type cmd and press Enter (This brings up the Windows Command Prompt
Type diskpart in the command prompt and press Enter (This launches the Diskpart utility within the Command Prompt window)
Now type list volume (This displays a list of all mounted volumes on your computer and their associated drive letters)
Type select volume 1 (or select any other volume as where the drive was present)
Now type assign letter R (Note: This sometime requires a reboot)
The drive will be available via Windows Explorer or My Computer.
Click Start -> Run (This brings up the Run dialog box)
Type cmd and press Enter (This brings up the Windows Command Prompt
Type diskpart in the command prompt and press Enter (This launches the Diskpart utility within the Command Prompt window)
Now type list volume (This displays a list of all mounted volumes on your computer and their associated drive letters)
Type select volume 1 (or select any other volume as where the drive is present)
Now type remove letter R (Note: This sometime requires a reboot)
Diskpart will now remove the drive letter.
The drive will no longer be available via Windows Explorer or My Computer.
Unhide
Now, should you want to unhide the drive and make it accessible again, just repeat the above process. But instead of typing remove letter R, type assign letter R
Click Start -> Run (This brings up the Run dialog box)
Type cmd and press Enter (This brings up the Windows Command Prompt
Type diskpart in the command prompt and press Enter (This launches the Diskpart utility within the Command Prompt window)
Now type list volume (This displays a list of all mounted volumes on your computer and their associated drive letters)
Type select volume 1 (or select any other volume as where the drive was present)
Now type assign letter R (Note: This sometime requires a reboot)
The drive will be available via Windows Explorer or My Computer.
When something goes wrong with Windows it can be very difficult to diagnose or repair, and there are times when booting your computer into Safe Mode just isn’t good enough. Safe Mode, a special diagnostic mode built into Windows strips the OS of all drivers and start-up software and presents you with a very limited version of Windows in which to diagnose what might be causing a problem, andrepair it. Many Windows features simply won’t operate in Safe Mode so there’s not very much you can do.
Fortunately though there is an alternative and it’s in every version of the operating system (XP, Vista and Windows 7). This is called “Safe Boot” and you can find it in the MSConfig panel. To open this type msconfig into the Start Menu search box in Vista or Windows 7, or run msconfig from the run option in XP.
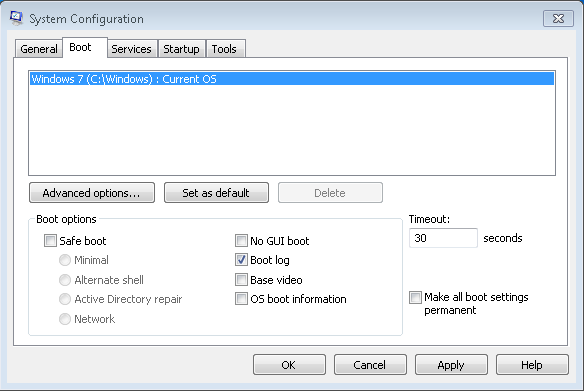
Under the Boot tab in the MSConfig window you’ll see the Safe Boot option as a tick box. Turning this on will make Windows use the SafeBoot option every time thereafter. When you want to stop using Safe Boot and return to starting Windows normally you’ll need to returnto the MSConfig panel and untick this option. There are also several other options here including Minimal Boot, which will take you intothe full Safe Mode, but the standard option willnormally be enough for most people.
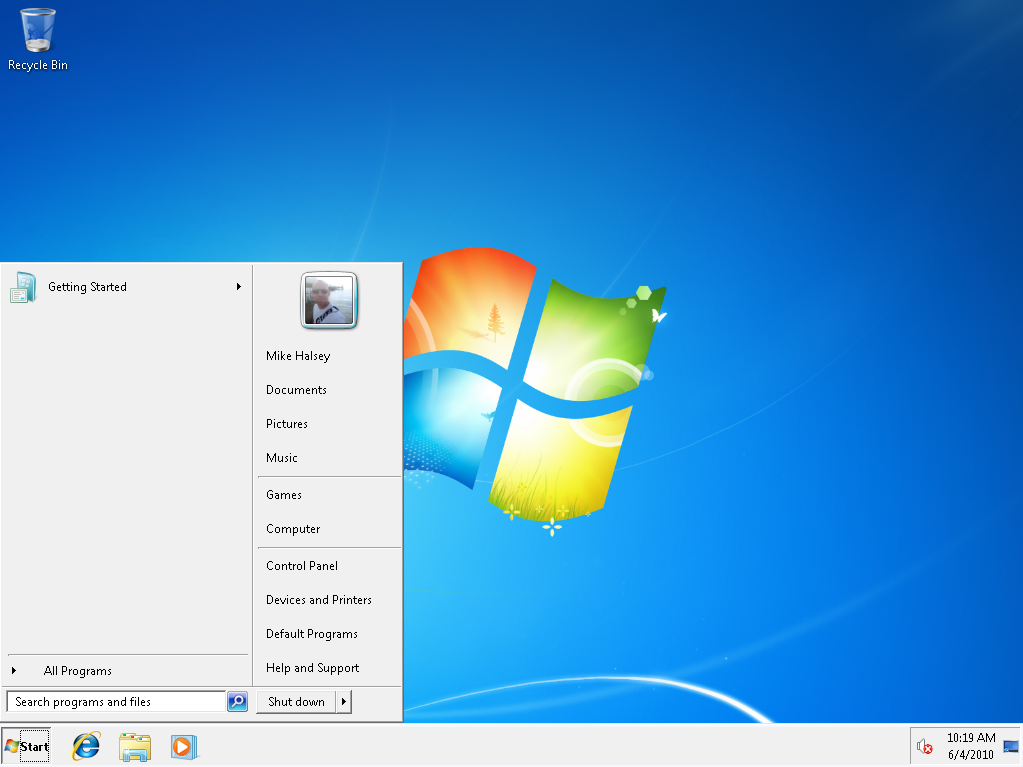
The Safe Boot screen, as you can see here is a half-way house between the full Windows desktop and Safe Mode. What you will find though is that most of your hardware drivers will be installed and working though your startup software will still be disabled.
So when might you want to use Safe Boot? Occasionally you will encounter a problem in Windows that you will need to go into Safe Mode to repair. As I mentioned earlier howeverSafe Mode won’t allow you to perform some Windows tasks, and this is where the Safe Bootmode is useful. You may also suspect that yourproblems aren’t being caused by a hardware driver, but by software instead. This diagnosticmode enables you to have a full Windows desktop where nothing loads at startup and where you can run and check programs individually to see what effect they are having on your system.
As I have already mentioned Safe Mode is extremely limiting, not just in the very low screen resolution that it gives you. If you needto run full diagnostics on your copy of Windows, to see what’s going on under the hood, or if you need to test individual software packages in a safe environment where they willbe able to run properly then Windows Safe Bootis the way to do it.
Remember though that you will need to turn off Safe Boot when you are done, or else Windows will start permanently in this mode. I have found this to be a very useful diagnostic tool in Windows and it’s extremely underused because, frankly, many people simply do not know that it exists. Hopefully you will find it useful too
Fortunately though there is an alternative and it’s in every version of the operating system (XP, Vista and Windows 7). This is called “Safe Boot” and you can find it in the MSConfig panel. To open this type msconfig into the Start Menu search box in Vista or Windows 7, or run msconfig from the run option in XP.

Under the Boot tab in the MSConfig window you’ll see the Safe Boot option as a tick box. Turning this on will make Windows use the SafeBoot option every time thereafter. When you want to stop using Safe Boot and return to starting Windows normally you’ll need to returnto the MSConfig panel and untick this option. There are also several other options here including Minimal Boot, which will take you intothe full Safe Mode, but the standard option willnormally be enough for most people.

The Safe Boot screen, as you can see here is a half-way house between the full Windows desktop and Safe Mode. What you will find though is that most of your hardware drivers will be installed and working though your startup software will still be disabled.
So when might you want to use Safe Boot? Occasionally you will encounter a problem in Windows that you will need to go into Safe Mode to repair. As I mentioned earlier howeverSafe Mode won’t allow you to perform some Windows tasks, and this is where the Safe Bootmode is useful. You may also suspect that yourproblems aren’t being caused by a hardware driver, but by software instead. This diagnosticmode enables you to have a full Windows desktop where nothing loads at startup and where you can run and check programs individually to see what effect they are having on your system.
As I have already mentioned Safe Mode is extremely limiting, not just in the very low screen resolution that it gives you. If you needto run full diagnostics on your copy of Windows, to see what’s going on under the hood, or if you need to test individual software packages in a safe environment where they willbe able to run properly then Windows Safe Bootis the way to do it.
Remember though that you will need to turn off Safe Boot when you are done, or else Windows will start permanently in this mode. I have found this to be a very useful diagnostic tool in Windows and it’s extremely underused because, frankly, many people simply do not know that it exists. Hopefully you will find it useful too
| |
|
File-sharing website Megaupload hasbeen swept up in so much drama lately it is beginning to rival a soap opera.
The frequent developments in the online piracy case may be hard to keep up with. So, here's a roundup.
The Site
On Jan. 19, the U.S. Justice Department and FBI shuttered Megaupload and had the company’s founder and other executives arrested in New Zealand for " massive worldwide online piracy ." Founder Kim Dotcom and three others appeared in court Friday andwere denied bail.
The hacker group Anonymous retaliated for the arrests by claiming responsibility for taking down websites run by Universal Music, the Justice Department and the Recording Industry Association of America. At the same time, bad guys were trying to take advantageof the situation by creating fake Megaupload sites so they could phish people.
The Bust
Dotcom, also known as Kim Schmitz and Kim Tim Jim Investor, spent his 38th birthday on Saturday in a NewZealand jail. But he didn't go quietly.
Details of his arrest are now comingout. Apparently, it was a dramatic, high-tech stand-off when dozens of New Zealand police backed by helicopters swarmed Dotcom's barricaded mansion to arrest him onFriday. Dotcom refused them entry and police had to cut their way through electronic locks to a safe room, where they discovered him with a sawed-off shotgun.
"Despite our staff clearly identifyingthemselves, Mr Dotcom retreated into the house and activated a number of electronic-locking mechanisms," Detective Inspector Grant Wormald from the Organised and Financial Crime Agency New Zealand told Reuters .
With Dotcom in cuffs, officers then began seizing things -- two guns, computers, documents and vehicles,lots of them. Personalized number plates on 20 or so seized vehicles included KIMCOM, HACKER, STONED, GUILTY, MAFIA, GOD and POLICE.
The Media
You wouldn't think it a believable story, but it turns out there were weird nuggets underlying The New York Post's claim that musician and producer Swizz Beatz was CEO of Megaupload. However, the top lawyer for Megaupload now says that Beatz was never officially the company's chief executive, reports VentureBeat .
"To my knowledge, Swizz Beatz was never involved in any meaningful way," Megaupload attorney Ira Rothken said, adding, remarkably that "He was negotiating to becomethe CEO, but it was never official." Beatz' publicist had earlier said Beatz was the CEO. Beatz was also briefly listed as CEO on Megaupload.com.
Media companies say the legitimate uses of sites like Megaupload are a veil concealing extensive theft but that doesn’t stop big-time stars, including Beatz’ wife, R&B singer Alicia Keys, from promoting it. Check out this video, which the Universal Music Group had the video taken down from YouTube, despite having no claim to the content. It has since been reinstated
The frequent developments in the online piracy case may be hard to keep up with. So, here's a roundup.
The Site
On Jan. 19, the U.S. Justice Department and FBI shuttered Megaupload and had the company’s founder and other executives arrested in New Zealand for " massive worldwide online piracy ." Founder Kim Dotcom and three others appeared in court Friday andwere denied bail.
The hacker group Anonymous retaliated for the arrests by claiming responsibility for taking down websites run by Universal Music, the Justice Department and the Recording Industry Association of America. At the same time, bad guys were trying to take advantageof the situation by creating fake Megaupload sites so they could phish people.
The Bust
Dotcom, also known as Kim Schmitz and Kim Tim Jim Investor, spent his 38th birthday on Saturday in a NewZealand jail. But he didn't go quietly.
Details of his arrest are now comingout. Apparently, it was a dramatic, high-tech stand-off when dozens of New Zealand police backed by helicopters swarmed Dotcom's barricaded mansion to arrest him onFriday. Dotcom refused them entry and police had to cut their way through electronic locks to a safe room, where they discovered him with a sawed-off shotgun.
"Despite our staff clearly identifyingthemselves, Mr Dotcom retreated into the house and activated a number of electronic-locking mechanisms," Detective Inspector Grant Wormald from the Organised and Financial Crime Agency New Zealand told Reuters .
With Dotcom in cuffs, officers then began seizing things -- two guns, computers, documents and vehicles,lots of them. Personalized number plates on 20 or so seized vehicles included KIMCOM, HACKER, STONED, GUILTY, MAFIA, GOD and POLICE.
The Media
You wouldn't think it a believable story, but it turns out there were weird nuggets underlying The New York Post's claim that musician and producer Swizz Beatz was CEO of Megaupload. However, the top lawyer for Megaupload now says that Beatz was never officially the company's chief executive, reports VentureBeat .
"To my knowledge, Swizz Beatz was never involved in any meaningful way," Megaupload attorney Ira Rothken said, adding, remarkably that "He was negotiating to becomethe CEO, but it was never official." Beatz' publicist had earlier said Beatz was the CEO. Beatz was also briefly listed as CEO on Megaupload.com.
Media companies say the legitimate uses of sites like Megaupload are a veil concealing extensive theft but that doesn’t stop big-time stars, including Beatz’ wife, R&B singer Alicia Keys, from promoting it. Check out this video, which the Universal Music Group had the video taken down from YouTube, despite having no claim to the content. It has since been reinstated
Total Pageviews
Connect With Us
Recommend us on Google!
Popular Posts
-
Antenna Theory: Analysis and Design, 3rd Edition Constantine A. Balanis CD
-
Download Google Chrome 35.0.1916.114 Final - Google Chrome Software
-
VeryPDF PDF Editor v2.6 + serial
-
Download CyberLink Director Suite 2.0 - collection of photo and video editing tools
-
Download HDClone Enterprise Edition 5.0.7 - backup software, hard disk data
-
Download HelpSmith 5.0.2 Build 14.624 - Advanced Software Help File
-
Optical Fiber Communications 4th ed Gerd keiser
-

Iobit.Security.360.v1.05
-
Physics of Semiconductor Devices: Simon M. Sze
-
How to download youtube videos






